📌 Key Takeaways:
Integration failures cause more resident platform rollouts to fail than feature gaps or user adoption issues.
SSO Architecture Splits by User Type: Staff authenticate through enterprise identity providers with SAML/OAuth while residents use email magic links or social providers, eliminating credential sprawl without forcing corporate authentication on community members.
Read-First Integration Prevents Data Contamination: Start with read-only PMS connections to validate sync accuracy, then enable selective write-backs only for specific state transitions like work order completions, keeping the property management system as the authoritative record.
Event-Level Logging Creates Audit Confidence: Capture who, what, when, where, and before-after states for every authentication and data change to enable incident investigation and prove compliance during security reviews.
Single-Building Pilots De-Risk Portfolio Rollouts: Test integration patterns in one community with defined success metrics like sync error rates below 1 per 1,000 records before expanding to additional properties.
Data Boundaries Must Be Visible: Create integration diagrams showing read/write permissions, system ownership, and data flow directions so technical and operations teams can spot drift before it causes conflicts.
Secure integrations happen by design, not by accident—and they determine whether your platform launch creates operational relief or months of troubleshooting.
For Class A community operations leaders evaluating resident experience platforms, these integration patterns provide the foundation for rollouts that enhance rather than complicate existing workflows.
Quiet confidence beats chaos.
A key fob beeps at the lobby door while the maintenance inbox fills with fifteen new requests. One password reset, one stale unit record, and your rollout plan starts wobbling.
You need a resident experience platform that plugs into the systems you already trust—without multiplying credentials, polluting data, or leaving audit gaps. Done well, integrations simplify life for residents and the property management team; done poorly, they create escalations and post-launch thrash.
A low-risk rollout rests on three pillars: enterprise-grade SSO to reduce credential exposure, a disciplined PMS integration that favors read-first and narrowly scoped write-backs, and clear data boundaries with event-level logging. These are widely adopted patterns in modern multifamily technology and align with recognized security standards.
Why Integrations Make or Break Resident Experience Rollouts
A resident experience platform connects daily touchpoints—community communications, amenity access and bookings, service requests, and more—into one surface. The upside is convenience and consistency. The risk surfaces during change: credential sprawl, data contamination from uncontrolled write-backs, and audit blind spots when events aren't captured at the right granularity.
These challenges aren't theoretical. They represent the most common reasons why resident experience platform rollouts extend beyond planned timelines and require expensive remediation work.
Plain-language summary: Keep identities unified, data ownership explicit, and every change traceable.
SSO First: Reduce Credential Risk and Admin Overhead
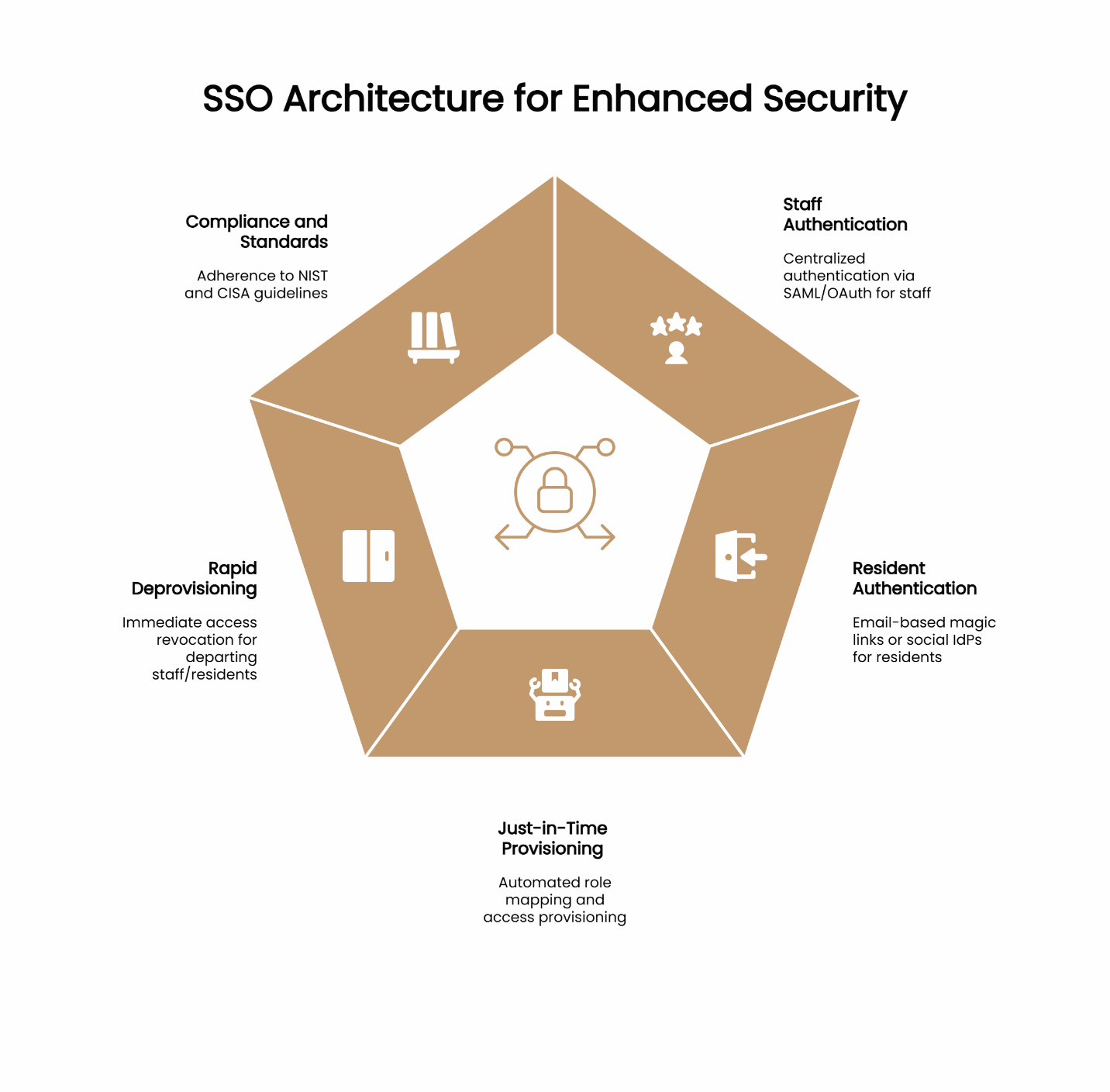
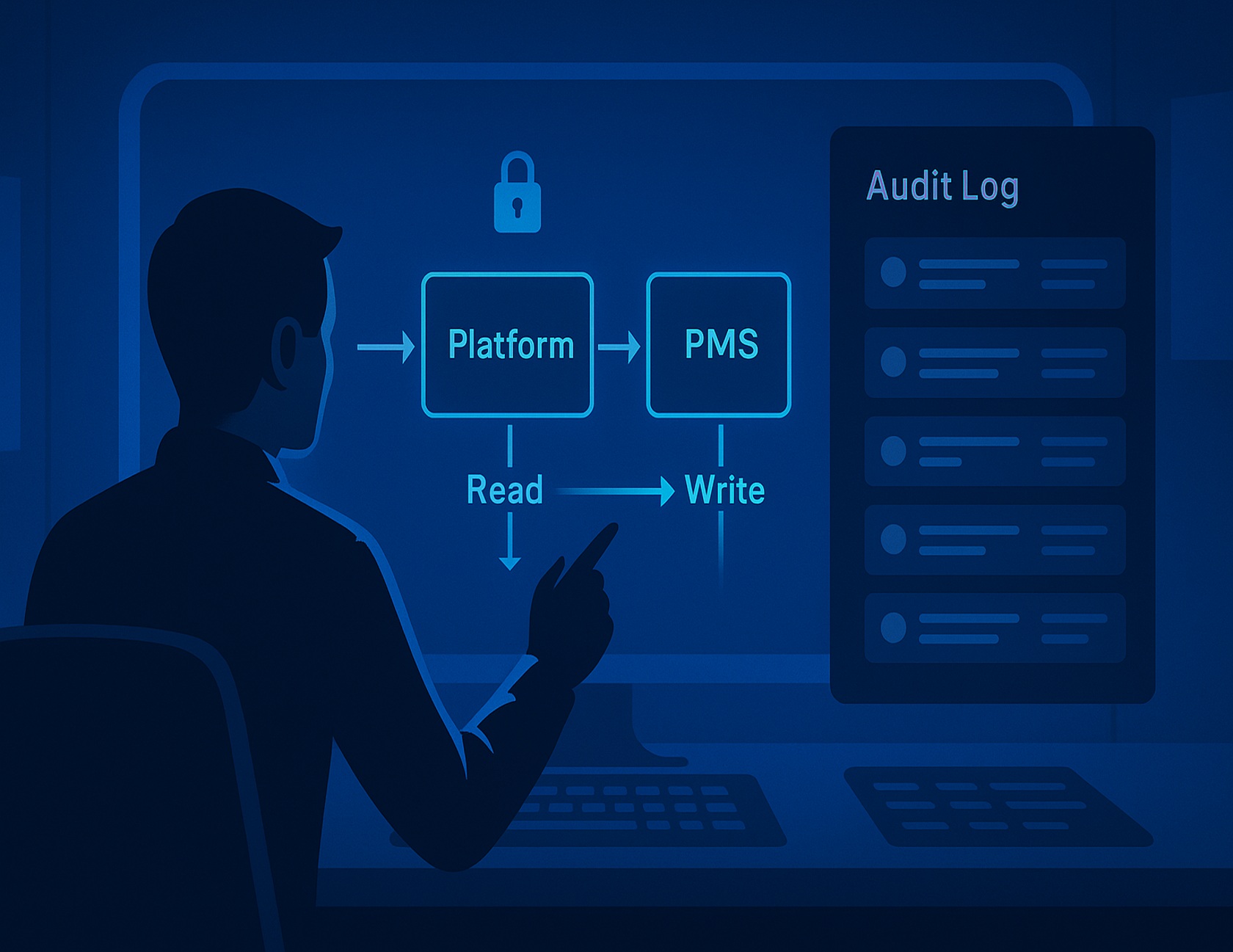
Enterprise SSO centralizes staff authentication through your Identity Provider (IdP) and enables Just-in-Time provisioning, role mapping, and rapid deprovisioning. Residents typically authenticate via email-based magic links or social IdPs rather than corporate credentials. This combination removes duplicate passwords, enforces least-privilege access, and speeds revocation—a meaningful risk reducer.
The architecture requires different approaches for different user types. Staff members connect through SAML or OAuth protocols against your existing directory services. Role and group mappings ensure that leasing consultants, maintenance technicians, and property managers receive appropriate access levels automatically through Just-in-Time provisioning.
Residents follow a different path. Corporate SSO rarely makes sense for this population. Email-based magic links or social identity providers offer the right balance of convenience and security while maintaining clear identity verification.
Time-to-revoke access becomes a critical operational metric. When staff members leave or residents move out, their system access must be terminated quickly and completely. Proper SSO architecture makes this process immediate rather than requiring manual updates across multiple platforms.
For authentication strength and identity assurance patterns, the NIST Digital Identity Guidelines provide comprehensive technical standards. For program-level SSO risk reductions and zero-trust alignment, CISA's guidance on Single Sign-On offers practical implementation approaches.
Operational wins to expect: fewer password resets, cleaner role enforcement across communities, and faster access revocation when staff transition out.
Key fact: SSO reduces credential risk and admin overhead.
Plain-language summary: One login system for staff, simple email links for residents, immediate access control when people leave.
PMS Integration Without the Heartburn
Start read-only. Prove your sync accuracy. Then add selective write-backs where they deliver clear value and won't corrupt the PMS as the system-of-record. The fundamental question centers on system of record versus system of engagement. The property management software typically maintains authoritative resident profiles, lease information, and financial records.
Define sync schedules and event triggers to avoid collisions. Rather than continuous synchronization, scheduled updates during low-activity periods reduce conflict potential. Event-driven updates handle time-sensitive changes like work order status modifications.
Safe Defaults for PMS Integration
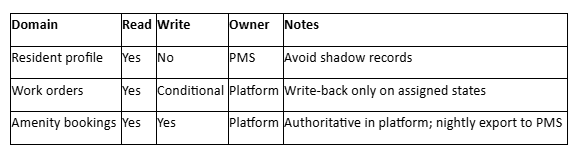
These defaults reflect common, conservative patterns that reduce incidents during rollout. Golden record ownership rules eliminate ambiguity during conflicts. When the PMS maintains resident contact information, the platform displays this data but doesn't modify it. When the platform manages amenity reservations, it exports summary data to the PMS for reporting purposes.
Consider this scenario: An operations leader planned to "go live" across three Class A buildings. The team left write-backs open for all work-order fields. A resident name correction in the platform overwrote the PMS's legal name. Leasing noticed during a renewal. One narrowly scoped write-back rule would have prevented the weekend clean-up.
From a data-governance perspective, aligning ownership and access with an information security management approach is prudent. The ISO/IEC 27001 information security management systems standard provides high-level principles for policy and process development.
Key fact: Write-back controls prevent data contamination.
Plain-language summary: Read everything you need, write back only what's essential, know who owns what data.
Data Boundaries That Prevent Contamination
Define the platform as the system-of-engagement and the PMS as the system-of-record—then draw the line clearly. Clear data boundaries prevent the contamination that derails integration projects. These boundaries define which system owns which data elements and under what conditions information flows between systems.
That line is enforced through:
- Write-back controls: Enable only the transitions you intend (e.g., work-order status updates from "assigned" to "completed")
- Data contracts with field-level mapping: Document type, owner, transform rules, and allowed directions (read/write)
- PII minimization and retention windows: Move only what the feature requires and keep it only as long as needed
But wait—there's a catch. A boundary that isn't visible during implementation tends to drift. This is where an at-a-glance artifact helps. Use an Integration Boundary Diagram that shows, in one page, read/write arrows, color-keyed system-of-record ownership, and SLA callouts across Identity & Access, Data Contracts, and Event Logging.
Retention windows align with business requirements and privacy regulations. Resident data might persist in the engagement platform for the duration of the lease plus a defined period for warranty or service follow-up. After expiration, automated purging ensures compliance without manual intervention.
Plain-language summary: Show teams exactly what flows, who owns it, and when it changes.
Proving It Works: Audit Events and Incident Review
Event-level audit is the safety net. Capture who did what, when and where, and before/after values for sensitive actions (authentication, data changes, admin operations). That level of detail enables SLA variance analysis and clean escalation runbooks when something goes wrong.
The logging framework should capture five key elements for every significant event: who initiated the action, what specific operation occurred, when the event took place, where in the system it happened, and the before-and-after state of affected data.
Authentication events require particular attention. Failed login attempts, successful authentications, privilege escalations, and access revocations all generate audit entries. This enables detection of credential attacks, privilege abuse, or access that should have been revoked but wasn't.
For control objectives and event coverage, NIST SP 800-53's Audit and Accountability controls provide comprehensive guidance on what to log and how to structure audit data for incident response.
Two practical approaches emerge across mature programs:
- Log where decisions happen: If a rule evaluates access on the platform, the platform must log it—even if the PMS is authoritative for the field
- Treat logs as data products: Standardize fields and retention so Security, Operations, and Support can query the same events without translation
Key fact: Event-level audit enables incident review.
Plain-language summary: Log everything important so you can prove what happened and fix what went wrong.
Pilot Plan: De-Risk With a Single-Building Rollout
Prove the pattern in one community before scaling. Single-building pilots provide controlled environments for validating integration patterns before full deployment. This approach limits potential issues while generating real-world operational experience.
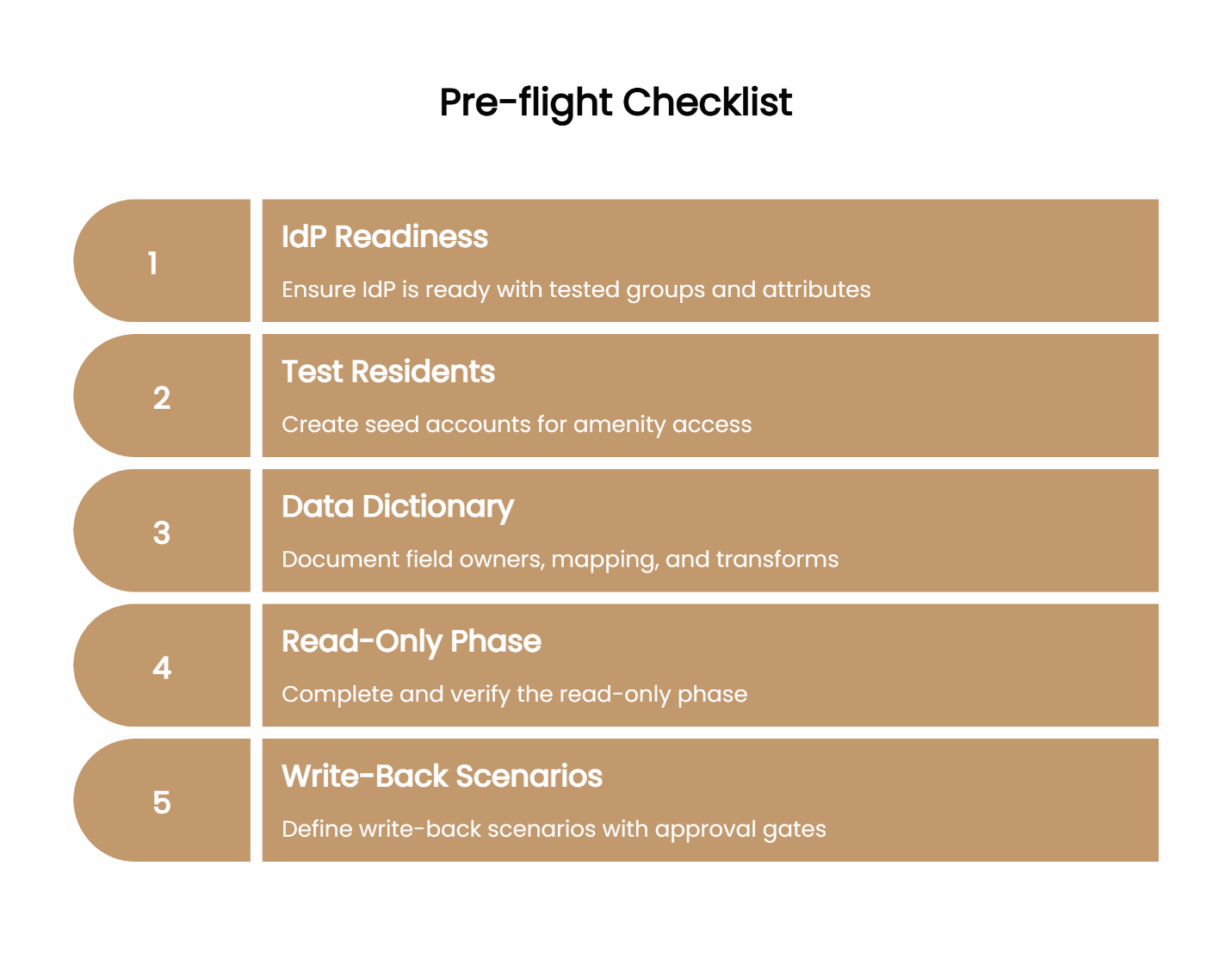
Pre-flight checklist:
- IdP readiness: Groups, attributes, and Just-in-Time provisioning tested
- Test residents: Seed accounts for amenity access and requests
- Data dictionary: Field owners, mapping, and transforms documented
- Read-only phase completed and verified
- Write-back scenarios defined with clear approval gates
Success indicators to monitor:
- High read rates on essential syncs
- Low access failures across resident and staff journeys
- Minimal sync errors per 1,000 records; investigate any spike before expanding scope
Change control and rollback gates: Define a small set of "stop-and-fix" conditions (e.g., profile collisions, duplicate bookings) and a reversible path. Scale only after stability holds for an agreed window.
The pilot phase typically runs for 30-60 days, depending on property size and integration complexity. This duration allows the system to handle month-end reporting cycles, resident move-ins and move-outs, and routine maintenance workflows.
Plain-language summary: Prove it small, measure stability, scale deliberately.
FAQ
Do residents need corporate SSO?
Corporate SSO isn't appropriate for residents. Staff should use enterprise SSO while residents can authenticate with email-based magic links or social IdPs. This keeps friction low for residents while maintaining strong controls for staff.
Can we integrate without write-back?
Integration can begin with read-only access from the PMS to the resident platform. Start read-only to validate data quality, then selectively enable write-backs with guardrails (e.g., specific state transitions). This phased approach reduces the risk of contaminating authoritative records.
What if our PMS lacks modern APIs?
Use scheduled CSV exports or an integration-platform-as-a-service as an interim step. Legacy systems without REST APIs can use these methods to provide functional integration while planning migration toward event-based sync when system upgrades become available.
For additional technical implementation guidance, see our integrating resident apps with existing property management software guide.
Enterprise SSO lowers credential exposure, conservative PMS write-backs keep the golden record clean, and granular audit trails give leaders confidence. That's how a resident experience platform goes live without drama. For broader context on platform orchestration, explore our unified resident experience platform framework and outcome-focused approaches in our engagement and retention solutions.
Secure. Predictable. Auditable.
Our Editorial Process:
We follow an evidence-first editorial standard: (a) we cite authoritative sources (standards bodies, .gov/.edu, and peer-reviewed/recognized publications), (b) subject-matter reviewers check technical accuracy and fairness, and (c) we periodically refresh articles to keep guidance current with policy and standards updates.
Author Byline & Bio:
The ElevateOS Insights Team. We partner with Property Management Teams to improve resident-facing operations in Class A Communities through technology and governed workflows. Learn more about ElevateOS.

.avif)


